
Comprehensive Security at the Gateway
Proactively stop malware, hacking attempts, phishing schemes and other threats before they reach users’ devices.
Next-Generation Filtering
Get a handle on every rogue application, encrypted web request, malware distribution point, drive-by malvertising attempt, and rash of spam.
Deep Analysis and Insights
Gain insights in real time from database-driven reports without the need for a separate appliance. See the network status at a glance on the dashboard, ensure compliance with full event logs, and get notifications of network anomalies or unusual user behavior with alert rules.
Superior Connectivity & Performance
Meet the challenges of a remote workforce, branch offices and guest Wi-Fi. Keep users and data safe regardless of location or level of access. Balance competing priorities, ensure Quality of Service (QoS) and maximize uptime while saving the organization money.
Can your employees work productively from anywhere using voice apps on their smartphones?
Conduct remote business meetings via web conferencing without requiring apps?
Service customer requests via website live chat?
With 3CX PBX they can do this and much more. The freedom of choice doesn’t end there, with 3CX you can choose to deploy on-premise on Windows or Linux, in your private cloud account or opt for 3CX to host your PBX for you. Whatever your preference, you are guaranteed to have professional support and quality. Get 3CX proof your business today!
Cheap:
Slash your phone bill and communications costs
Responsible:
Never miss a Call – Use Android & iOS apps application on your phone, even if you are out of office
Flexible:
Status, Chat, Click2Call, CRM Integration


Your mission-critical data, always available
- Backup and recovery solution that always works
- Full ecosystem compatibility
One solution, seamless deployment
- Works across any cloud, virtual or physical environment
- Meet your requirements today and in the future
Fewer resources required
- Reduce administrative overhead and labor costs
- A single platform supporting data backup, recovery and management
Audit and Compliance
Provides General Data Protection (GDPR) compliance capabilities and data security with Veeam DataLabs™ and Veeam ONE™
Disaster Recovery
- Granular restores of VM directly from agentless backups
- Instant recovery of all VMs
- Automated disaster recovery testing of VM backups
- Minimize downtime and disruption using integrated bare-metal disaster recovery, physical to virtual (P2V) and virtual to physical (V2P) recovery
Cloud Data Protection
- Instant Cloud Recovery integrates with Azure Site Recovery to provide a DRaaS with near-zero RPO and RTO
- Certified cloud connectors for all major cloud vendors
- Support for all AWS cloud storage tiers
- Optimize storage costs and bandwidth with in-line deduplication
Security and Compliance
- Ransomware Resilience protects your backup data from external attacks
- Ensure your data is compliant in every location
- Ensure your data is compliant with GDPR Guard
- Store credit card transaction data securely
Easy to use
- Manage your entire data ecosystem from a single console
- Eliminate need for multiple point products
- Set up backup jobs in a few clicks
- Easily track every backup, replication and recovery job
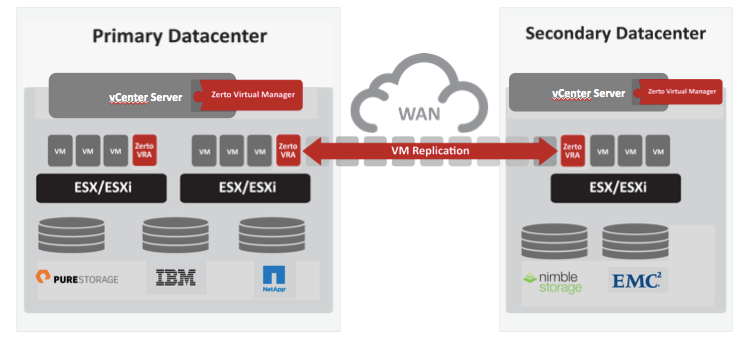
IT Resilience
The only all-in-one IT Resilience Platform, converging Disaster Recovery, Backup and Cloud Mobility in one simple, scalable platform.
Cost Effective
Reduce cost and complexity of application migrations and data protection with Zerto’s unique platform utilizing Continuous Data Protection.
Automation
Orchestration built into the platform enables full automation of recovery and migration processes.
24/7 Control
Analytics provides 24/7 infrastructure visibility and control, even across clouds.
Ready-to-Deploy Applications
Set it ‘n Forget it
Deploy Almost Anything
Multi-Admin Access With a Shared Database
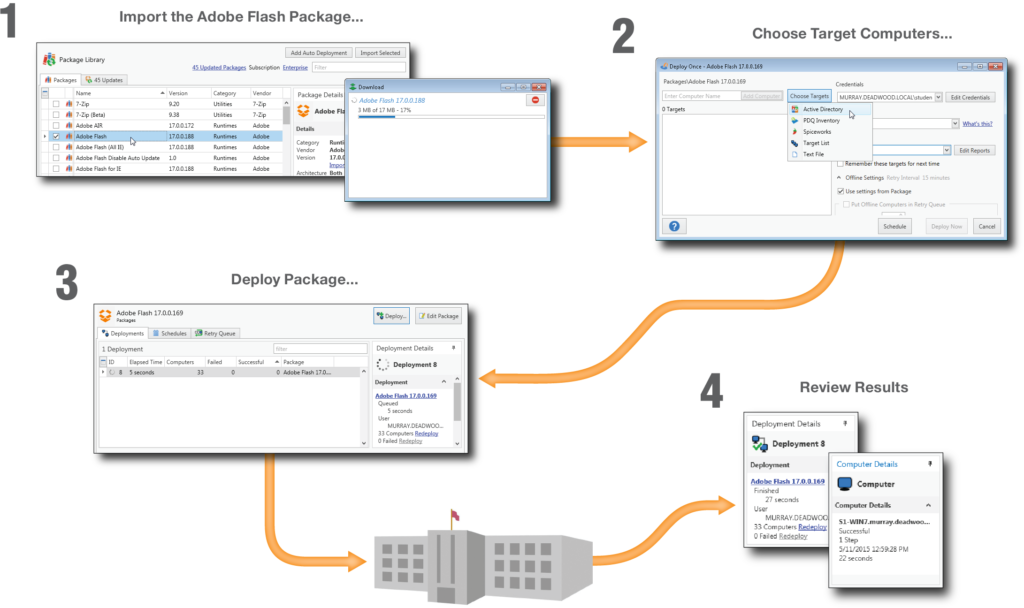
Reports
Inventory Tools
Intelligent Data Tracking
Integration with PDQ Deploy

Fast
connection
NetSupport Manager is designed to work over a LAN, WAN or the internet, with support for both TCP/IP and HTTP communications (and even legacy IPX and NetBIOS support).

Multi-platform support
Remotely support any Windows, Mac, Linux (legacy) and/or Chrome OS desktop, as well as a range of mobile devices, from your Windows PC, Mac, Apple iOS/Android tablet or smartphone.

Manage devices simultaneously
NetSupport Manager provides one-to-many support, not just 1:1, meaning you can scan and view multiple screens in sequence via unique real-time thumbnails.
Systems management
From detailed hardware/software inventory, and grouping devices into a clear hierarchy to remote command prompt and registry editor, gain a detailed overview of your IT infrastructure.

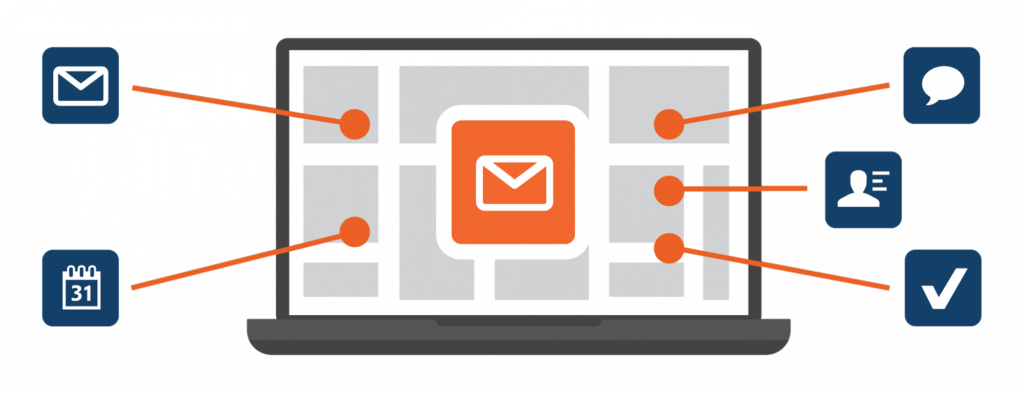
Email, calendar, contacts and more
Kerio Connect is an award-winning, messaging and collaboration solution, that meets the needs of small and mid-sized businesses by offering a robust feature lineup.
Instant messaging
Instant messaging with Kerio Connect is flexible. It is built in to the Kerio Connect Client and also supports all XMPP chat clients.
Mobile device support
Offer your users smooth and seamless support for their mobile device of choice.
Admin friendly server and user management
Administer email, calendaring and other critical functionality easily and efficiently.
High availability
With high-availability, if a crash or failure occurs your second Kerio Control machine jumps into action. Users see no drop of service. You have no vulnerability exposure.
Next-generation firewall capabilities
Kerio Control brings together next-generation firewall capabilities — including a network firewall and router, intrusion detection and prevention (IPS), gateway anti-virus, VPN, and web content and application filtering.
Simple and secure VPN
Link headquarters to remote users and branch offices securely and easily. Kerio’s own VPN tunneling with dead-simple setup requires minimal configuration, and provides a high-performance network connection. You can also use industry-standard IPsec/L2TP for connectivity from mobile devices or third-party firewalls.
Unmatched Quality of Service
Easily prioritize and monitor network traffic to guarantee high-speed transmission for the most important traffic types. Internet Link Load Balancing optimizes Internet access by distributing traffic across multiple links.

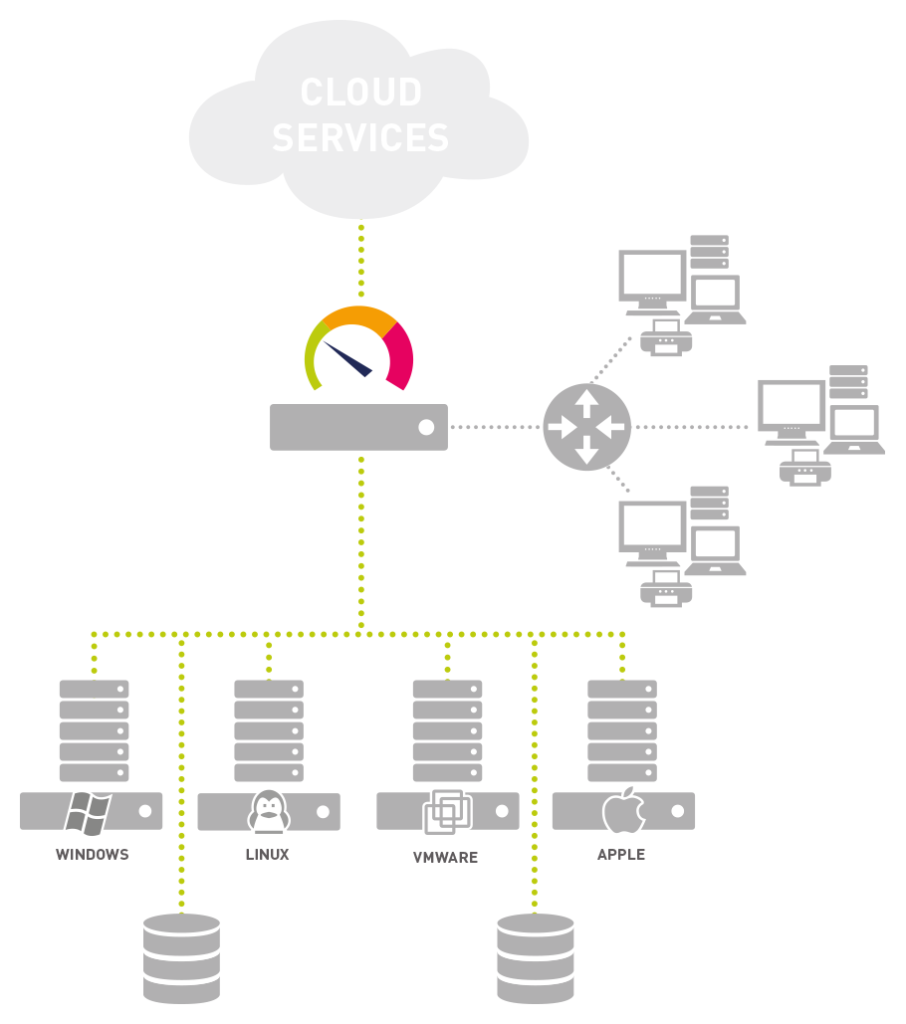
Monitor
- Monitoring and alerting you about uptimes and downtimes or slow servers
- System health monitoring of your various hardware devices
- Network device monitoring and bandwidth accounting
- Application monitoring
- Monitoring virtual servers
Prevent
- Service level agreement (SLA) monitoring
- System usage monitoring (for example, CPU load, free memory, or free disk space)
- Database performance and table values monitoring
- Email server monitoring and reviewing various backup solutions
- Monitoring your network’s physical environment
Predict
- Classifying network traffic by source or destination, as well as content
- Discovering unusual, suspicious, or malicious activity with devices or users
- Measuring Quality of Service (QoS) and Voice over IP (VoIP) parameters
- Cloud monitoring services
- Discovering and evaluating network devices
Control
- Collecting system information for various hardware types
- Finding unexpected relationships between your network components to detect potential security issues and assessing the real usage of your network and hardware
- Fail-safe monitoring using a failover cluster setup
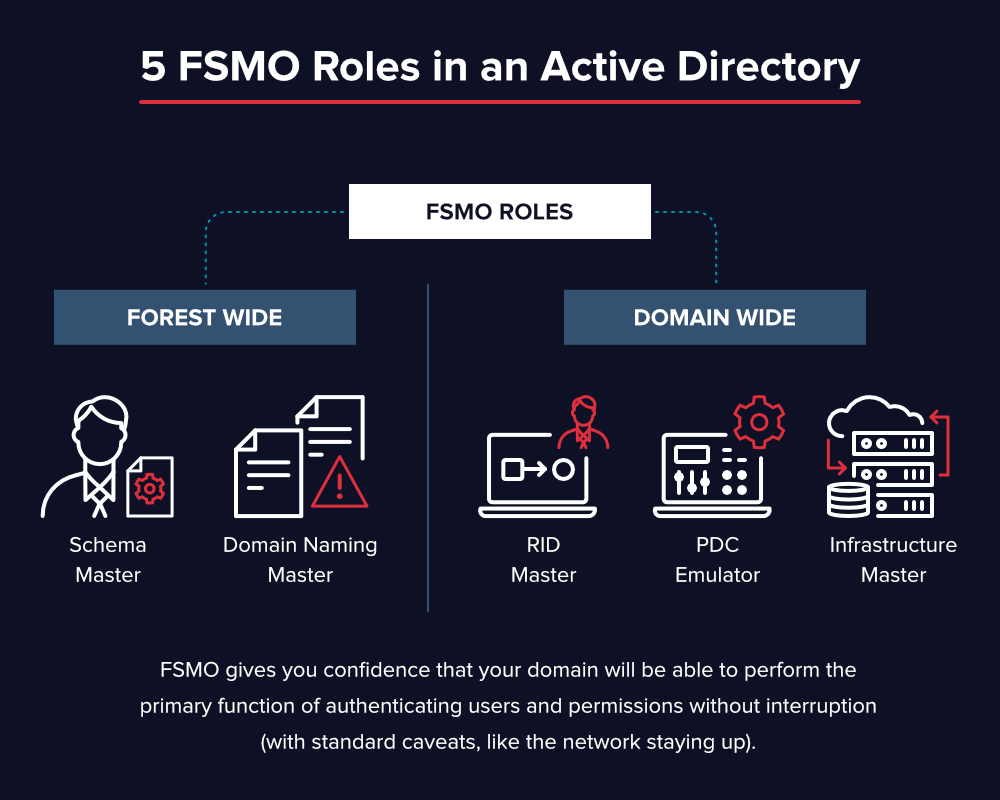
Domain Services
stores centralized data and manages communication between users and domains; includes login authentication and search functionality
Certificate Services
creates, distributes, and manages secure certificates
Lightweight Directory Services
supports directory-enabled applications using the open (LDAP) protocol
Rights Management
protects copyrighted information by preventing unauthorized use and distribution of digital content

Office 365 Subscriptions
Office 365 is Microsofts subscription-based version of its ubiquitous office software suite. Access to all the familiar programs such as Word, Excel, PowerPoint and Outlook, plus much more is available without the large, one off purchase price of days gone by.
Being cloud based Office 365 is accessible from anywhere. If you’ve got an internet connection and a device then you can access Office 365. The gives complete flexibility for businesses with remote employees, multiple locations or companies with employees that travel a lot.
The subscription model means that you are constantly up to date too. Microsoft are consistently adding to and upgrading the Microsoft Office suite. With a subscription the whole business will always be on the latest, best version. The updates install automatically with no need to roll them out; so no uninstalls and re-installs to do.
Industry Leading
Cross-Platform DLP
Discover, monitor, and protect your sensitive data with Endpoint Protector, advanced multi-OS data loss prevention.
Device Control
Lockdown, Control and Monitor USB and peripheral ports to stop data theft and data loss
Content-Aware Protection
Content inspection and contextual scanning of data for removable devices and applications like Outlook, Skype, Dropbox and others
Enforced Encryption
Encrypt, manage and secure USB storage devices by safeguarding data in transit. Password-based, easy to use and very efficient

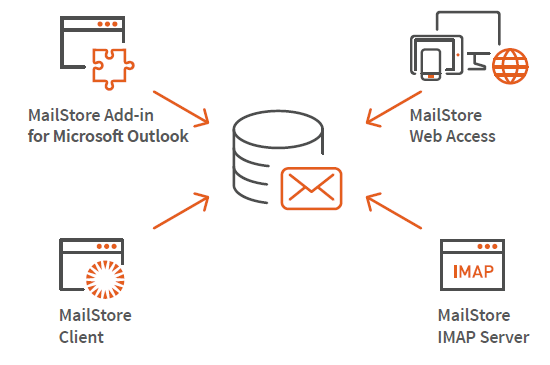
Advantages for your Company
- Assistance with regulatory compliance
- Help with fulfilling GDPR obligation
- Fast full-text searching for emails and attachments
- Protection against data loss
- Reduce the workload of email servers
- Save up to 70% storage space
- Simplify backup and restore
- Independence of cumbersome PST files
- Eliminate mailbox quotas
- See all advantages
Supported Email Systems
- Microsoft Exchange Server 20031, 20071, 2010, 2013, 2016 and 2019
- Microsoft 3652
- G Suite
- All IMAP or POP3-compatible email servers
- MDaemon, IceWarp and Kerio Connect
- PST, EML and other email files
- Email clients such as Microsoft Outlook
- See all technical specifications
TSplus Enterprise Edition:
- Easy management. Robust security. Cross-Platform compatibility.
- Brings scalability.
- Advanced Remote Desktop and Application Publishing
- Tools you need to operate TSplus in a Multi-Server environment
- Farm Manager and Load Balancing
TSplus Enterprise Plus Includes:
Cyber crime is one of the greatest threats to an online business.
Enterprise Plus will protect your TSplus servers from online criminals and will create a secure environment for your users.
- Enterprise Edition
- Two Factor Authentication
- Ultimate Protection
- Server Genius
- Virtual Printer



Features Overview
- Homeland Protection
- Brute Force Defender
- Global IP Management
- Permissions Control
- Working Hours Restrictions
- Ransomware Attacks Shield
Stop Ransomware Attacks*
Ransomware is the most significant of today’s cyber threats. Attackers can encrypt or even permanently delete your data. Paying the ransom is no guarantee that your data will be restored. The best way to deal with ransomware is to stop it before attackers have the chance to disrupt your server. TSplus Advanced Security Ransomware Protection will efficiently detect and block ransomware attacks.
TSplus Advanced Security instantly warns you as soon as it detects a ransomware activity on your system, providing you with the list of the infected items to quarantine. You get detailed information about the attack source to avoid this issue in the future. You can easily whitelist the programs you know as safe via the “Advanced Settings” tab.
TSplus Enterprise Edition:
Out of necessity, millions of workers have been dispersed from their classic central office surroundings.
The cost and logistics of duplicating software licenses alone can be enormous.
Using Remote Work to access corporate desktop PCs can save organizations enough money in licensing costs to pay for itself on the first day of deployment.



Maximum Performance. Guaranteed
Diskeeper & V-locity are now DymaxIO! Boost Windows & SQL application performance at least 30-40% or more. DymaxIO fixes Windows performance problems such as application slows and freezes, at the source.
Instant File Recovery
Undelete recovers deleted files from network drives & servers instantly. It’s quick – no need to go to backup. Increase your security, protection, & reliability with Undelete.
Key Features
- Centrally manage syslog messages
- Receive real-time alerts based on syslog messages
- Automatically respond to syslog messages
- Store and archive logs for regulatory compliance
- Schedule the generation of syslog reports via email
- View syslog data anywhere with secure web access


Employee Monitoring
Monitor employee activity with customizable reports to identify team, department, individual level productivity, social media use, time spent on projects, apps, and more.
User Behavior Analytics
Identify behavior anomalies and uncover potential threats in real time. Get fully customizable alerts with full audit trail and video recording of all user actions.
Data Loss Prevention
Leverage Teramind’s industry-defining DLP features such as OCR, fingerprinting, and content discovery to prevent malicious or negligent data exfiltration.
User Activity Monitoring
Monitor and control user activity to ensure compliance with internal security policies and regulatory requirements.
Compliance & Audit
Ensure ongoing compliance for GDPR, HIPAA, PCI and much more by identifying and alerting user to non-compliant actions with real time alerts.
Insider Threat Prevention
Automate risk detection and block unwanted employee behavior. Teramind uses smart rules & alerts to always keep your organization safe.